Why won cracking bitcoin wallets
Bitcoin wallets are a popular target for hackers due to the potential for financial gain. Understanding how these wallets can be cracked is crucial for protecting your assets. The following articles explore different methods and techniques used to crack bitcoin wallets, providing valuable insights on how to enhance security measures.
The Art of Cracking Bitcoin Wallets: Techniques and Tools
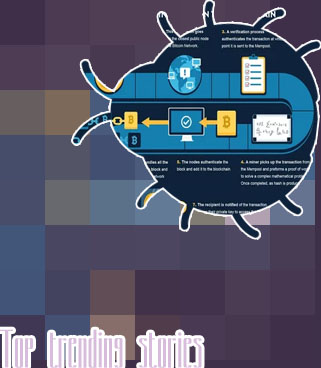
"The Art of Cracking Bitcoin Wallets: Techniques and Tools" is a comprehensive guide that delves into the intricate world of cryptocurrency security. Written by experts in the field, this book provides valuable insights into the techniques and tools used by hackers to gain unauthorized access to Bitcoin wallets.
One practical use case of the information provided in this book is for individuals looking to enhance the security of their own Bitcoin wallets. By understanding the methods used by hackers, users can take proactive measures to safeguard their digital assets. Implementing strong passwords, enabling two-factor authentication, and regularly updating wallet software are just a few of the strategies outlined in the book that can help prevent unauthorized access to Bitcoin wallets.
The authors of this book have done an excellent job of breaking down complex concepts into easy-to-understand language, making it accessible to readers of all levels of expertise. Whether you are a seasoned cryptocurrency enthusiast or a beginner looking to learn more about Bitcoin security, "The Art of Cracking Bitcoin Wallets: Techniques and Tools" is a valuable resource that will equip you with the knowledge needed to protect your digital assets.
Protecting Your Bitcoin Wallet: Tips to Prevent Hacking
In the fast-evolving world of cryptocurrency, safeguarding your Bitcoin wallet against hacking is paramount. With the surge in popularity of digital currencies, hackers are constantly on the lookout for vulnerabilities to exploit. By implementing a few key strategies, you can significantly reduce the risk of falling victim to cyber theft.
One crucial tip to enhance the security of your Bitcoin wallet is to enable two-factor authentication. This adds an extra layer of protection by requiring not only a password but also a second form of verification, such as a unique code sent to your mobile device. Additionally, regularly updating your wallet software and using strong, unique passwords can help thwart potential hackers.
Another effective method to safeguard your Bitcoin holdings is to store them offline in a hardware wallet. These physical devices are not connected to the internet, making them immune to online attacks. By keeping your Bitcoins in a hardware wallet, you can enjoy peace of mind knowing that your assets are safe from cyber threats.
A practical use case demonstrating the benefits of implementing these security measures is when a Bitcoin investor stored their holdings in a hardware wallet and enabled two-factor authentication. When a phishing attempt was made to steal their login credentials, the hacker was unable to access the wallet due to the additional layer of security. As a result, the investor's Bitcoins remained safe
Inside the Mind of a Hacker: Strategies for Cracking Bitcoin Wallets
In the ever-evolving landscape of cybersecurity, understanding the strategies employed by hackers is crucial in order to protect oneself from potential threats. The article provides valuable insights into the methods hackers use to crack Bitcoin wallets, shedding light on the vulnerabilities that exist within this digital currency ecosystem.
One practical use case of this knowledge is in the prevention of cyber attacks targeting individuals or organizations holding Bitcoin. By being aware of the common strategies used by hackers to gain access to Bitcoin wallets, users can take proactive measures to secure their assets and mitigate the risk of theft. For example, implementing multi-factor authentication, using hardware wallets, and regularly updating security measures are effective ways to safeguard Bitcoin holdings from unauthorized access.
Furthermore, understanding the mindset of hackers can also empower individuals and businesses to enhance their overall cybersecurity posture. By thinking like a hacker, organizations can anticipate potential vulnerabilities and develop robust defense mechanisms to protect against potential threats. This proactive approach can ultimately lead to a positive outcome, such as preventing a cyber attack and safeguarding sensitive information from falling into the wrong hands.
Overall, the article serves as a valuable resource for individuals looking to enhance their understanding of cybersecurity threats and take proactive steps to safeguard their digital assets. By gaining insights into the strategies employed by hackers, users can better protect themselves in an increasingly digital world
